- Community home
- Community
- Archive
- Vodafone Connect Router - Starting the VPN client
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ask
Reply
Solution
Vodafone Connect Router - Starting the VPN client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
29-03-2017 11:55 AM
In the router, using 'Expert mode' under Settings -> Configuration there's a VPN settings section where it lets you configure the router as various VPN client types.
Does anyone know how to start the VPN having entered the settings in there? Having entered the various details for the 'L2TP Client' there doesn't seem it doesn't seem to be starting automatically as there's nothing in either the routers own event log, or anything (even failures) in the servers logs.
I can connect via L2TP clients running on IOS and Windows so I know there's nothing fundamentally wrong that would stop the router from connecting.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
29-03-2017 01:20 PM
Having dug around in the router, I've found out the router is trying to connect with the VPN automatically once configured, the bad news is it's constantly failing for some reason.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
29-03-2017 02:31 PM
It the software that just keeps on giving. Let me know how it turns out for you - it seems that some of the setting it wants like subnet and ip address for remote network are not particularly standard for commercial VPN services - most just expect to allocate you based on DHCP - it is not entirely clear what this client here actually expects.
And as you say where is the logs vodafone ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
29-03-2017 02:46 PM
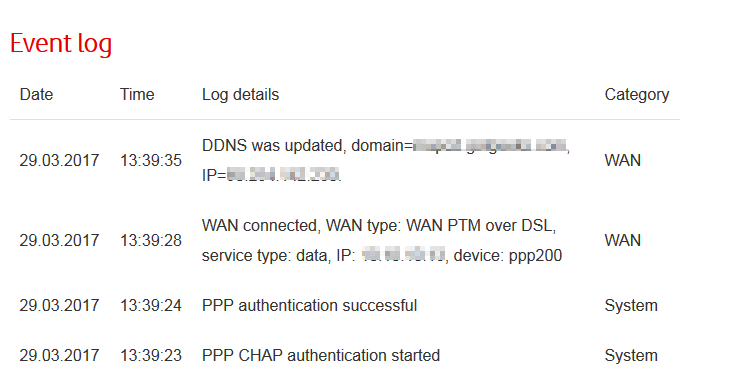
Just noticed I do see entries in the log however unfortunately my traffic is not then routed through the ppp200 connection, so to all intents and puposes I may have a vpn connection live but my interenet traffic seems to remain routed through the normal route rather than the vpn.
And there is no switch to allow routing via the ppp200 connection. Sigh!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
29-03-2017 03:58 PM
Not too sure what is going on with it; it's trying to connect to an Ubiquiti EdgeMax device and all I can get out of the servers StrongSwan log is the following ad infinitum.
01[CFG] looking for pre-shared key peer configs matching 81.X.X.X...90.253.Y.Y[90.253.Y.Y]
01[CFG] selected peer config "remote-access"
01[IKE] IKE_SA remote-access[355] established between 81.X.X.X[81.2.123.226]...90.253.Y.Y[90.253.Y.Y]
01[ENC] generating ID_PROT response 0 [ ID HASH ]
01[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (68 bytes)
14[NET] received packet: from 90.253.Y.Y[500] to 81.X.X.X[500] (68 bytes)
14[IKE] received retransmit of request with ID 0, retransmitting response
14[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (68 bytes)
04[IKE] sending DPD request
04[ENC] generating INFORMATIONAL_V1 request 748921213 [ HASH N(DPD) ]
04[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (92 bytes)
16[NET] received packet: from 90.253.Y.Y[500] to 81.X.X.X[500] (68 bytes)
16[IKE] received retransmit of request with ID 0, retransmitting response
16[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (68 bytes)
01[IKE] sending DPD request
01[ENC] generating INFORMATIONAL_V1 request 200738114 [ HASH N(DPD) ]
01[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (92 bytes)
16[NET] received packet: from 90.253.Y.Y[500] to 81.X.X.X[500] (68 bytes)
16[IKE] received retransmit of request with ID 0, retransmitting response
16[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (68 bytes)
10[NET] received packet: from 90.253.Y.Y[500] to 81.X.X.X[500] (296 bytes)
10[ENC] parsed ID_PROT request 0 [ SA V V V V V V ]
10[IKE] received DPD vendor ID
10[IKE] received NAT-T (RFC 3947) vendor ID
10[IKE] received draft-ietf-ipsec-nat-t-ike-03 vendor ID
10[IKE] received draft-ietf-ipsec-nat-t-ike-02 vendor ID
10[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
10[IKE] received draft-ietf-ipsec-nat-t-ike-00 vendor ID
10[IKE] 90.253.Y.Y is initiating a Main Mode IKE_SA
10[ENC] generating ID_PROT response 0 [ SA V V V ]
10[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (132 bytes)
02[NET] received packet: from 90.253.Y.Y[500] to 81.X.X.X[500] (292 bytes)
02[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
02[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
02[NET] sending packet: from 81.X.X.X[500] to 90.253.Y.Y[500] (308 bytes)
03[NET] received packet: from 90.253.Y.Y[500] to 81.X.X.X[500] (68 bytes)
03[ENC] parsed ID_PROT request 0 [ ID HASH ]
I suspect they can't agree on something, that said at least we know the Vodafone (Hauwei) router is using FreeSwan (v1.92) for IPSec so there are some docs available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
30-03-2017 12:52 PM
Hi @nigel84894
Thanks for getting in touch.
For help with this, please speak to our Broadband team on Live Chat.
Thanks,
- Vodafone does not pay my bonus I am entitled to in Off topic
- Problem with Hotspot Ticket in Off topic
- The Vodafone Community Hub: Connecting Users, Sharing Insights, and Fostering Digital Dialogue in Off topic
- Network update: 4 September 2023 in Latest news
- Vodafone is incorrectly blocking my website in Off topic